Self-Hosting Pangolin on Unraid: Transitioning to a VM-based Setup
08 Mar 2025Self-Hosting Pangolin on Unraid
Pangolin is an exciting new tool designed to simplify remote access to self-hosted resources, bypass CGNAT issues, and seamlessly integrate with security tools such as Crowdsec. With its recent 1.0 release, Pangolin continues to evolve, incorporating powerful new features.
Why Switch to a VM-Based Setup?
In my experience, the optimal approach to using Pangolin on Unraid is to bypass the official Unraid installation guide provided by Fossorial and instead deploy Pangolin within an isolated virtual machine (VM). This method simplifies the integration with Crowdsec and leverages Docker Compose for easier management.
Steps to My Transition
Network Configuration
- Created a dedicated VLAN specifically for Pangolin.
- Configured firewall rules to allow outbound traffic only, preventing communication with other internal networks.
- Enabled administrative access from trusted local networks.
Unraid Configuration
- Established a new network interface linked directly to the VLAN.
Virtual Machine Setup
- VM Specs: 4 CPU cores, 4 GB RAM (additional resources allocated for Crowdsec).
- Set networking to default settings within the VM for simplicity.
- Mounted shared host files via VirtioFS at
/pangolinto enable easy backups of configurations and logs. - Installed Pangolin using the Fossorial Quick Install Guide.
Cleanup and Streamlining
Transitioning to a VM allowed me to simplify my setup by removing several Docker containers previously managed in Unraid:
- Pangolin
- Gerbil
- Traefik
- Crowdsec
Newt Configuration
- Adjusted the networking setup within Unraid Community Applications.
- Added two custom networks, and left the built in unraid networking field blank.:
- New VLAN (
br3), assigned a manual IP due to networking conflicts. - Docker network (
fossorial) for containers accessed through Pangolin and Newt.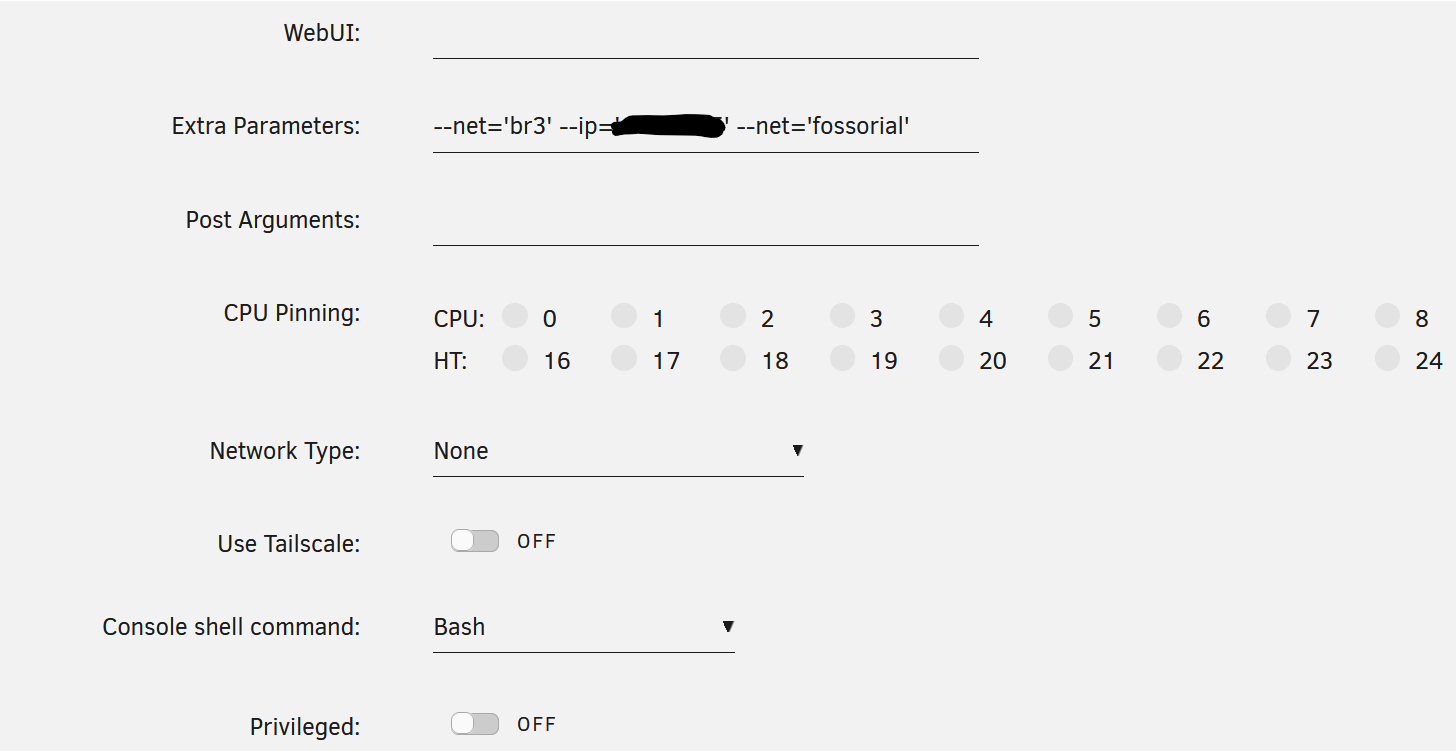
- New VLAN (
- Generated Newt ID and secret, configuring these as container variables from the new Panolin install.
Crowdsec Integration
The VM setup significantly simplified Crowdsec integration, particularly through tools like Crowdsec Manager, enabling straightforward management of enrollments, whitelists, and custom security scenarios including Cloudflare Turnstile.
Enhanced Security with Cloudflare Tunnels
To further enhance security, I’m utilizing Cloudflare Tunnels with their WAF. The tunnel is hosted via Unraid Community Applications within the dedicated VLAN. The traffic flows as follows:
Cloudflare → Cloudflare Tunnel → Pangolin VM (with Crowdsec) → Newt → Docker Containers (Unraid)
For accurate IP address detection through Cloudflare, I’m using the Traefik Real-IP Plugin.
Future Plans
My next step is integrating Crowdsec directly with Cloudflare’s WAF to shift blocking responsibilities away from Traefik. Previously attempted IPS and geoblocking solutions with UDM Pro proved resource-intensive, reaffirming my preference for Cloudflare’s robust security.